Social Engineering
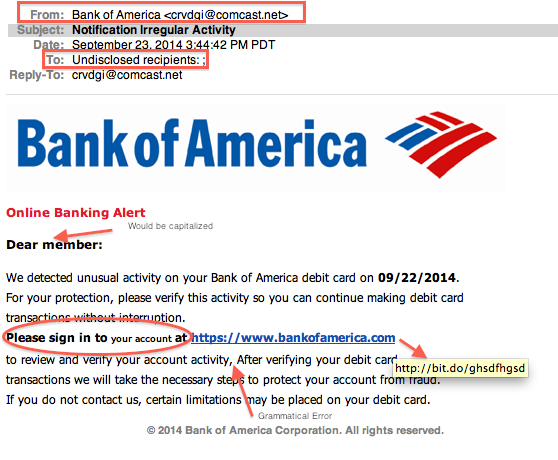
Social Engineering is a tool hackers use to extract information without the use of any coding. One common attack is email Phishing. This is often done by appearing to be an authentic source in order to get sensitive information. By gaining enough personal information, a hacker is then able to take advantage of weak security protocols and potentially cause more damage. This can be done in several steps. For example, information gathering>hook>execution.
The information gathering stage relies on using little information to gain more. They will also scout companies that the target is associated with; to see how strong or weak their security protocol is. By this I am referring to how much information those companies will reveal. For example, usually banks have a much more secure protocol. (You’ll find that banks will not be willing to speak to you if get a security question wrong).
However, a utilities company (phone, broadband, water, etc) is more lenient/forgiving in comparison. By identifying an associated company with a weak security protocol, you’ll be surprised how much information you’re able to gather with such little information to start with. The method above is called Vishing, a combination of voice and phishing. The following image is an example of a email phishing attempt.